New article published in IEEE Communications Surveys & Tutorials
Quantum Cryptography in 5G Networks: A Comprehensive Overview
Authors
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
- VSB – Technical University of Ostrava, Ostrava, Czechia
- Libor Michalek
- VSB – Technical University of Ostrava, Ostrava, Czechia
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
- Patrik Burdiak
- VSB – Technical University of Ostrava, Ostrava, Czechia
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
- Jan Rozhon
- VSB – Technical University of Ostrava, Ostrava, Czechia
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
- Filip Richter
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
- Filip Lauterbach
- VSB – Technical University of Ostrava, Ostrava, Czechia
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
-
- Department of Telecommunications, Faculty of Electrical Engineering, University of Sarajevo, Zmaja od Bosne bb, Sarajevo, Bosnia and Herzegovina
- Peppino Fazio
- DSMN, Ca’ Foscari University, Venice, Italy
- VSB – Technical University of Ostrava, Ostrava, Czechia
- Miroslav Voznak
- VSB – Technical University of Ostrava, Ostrava, Czechia
Abstract
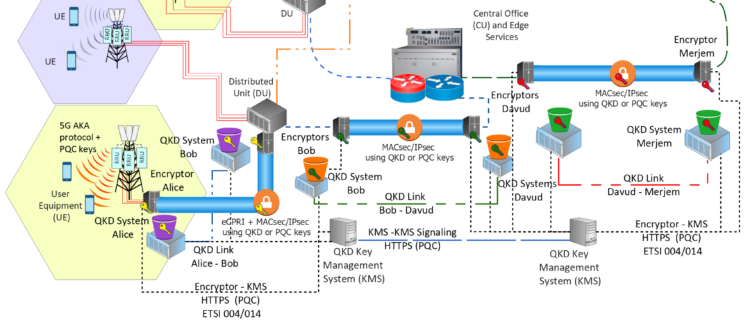
Every attempt to access to the Internet through a web browser, email sent, VPN connection, VoIP call, instant message or other use of telecommunications systems involves cryptographic techniques. The most commonly applied technique is asymmetric cryptography, which is generally executed in the background without the user even being aware. It establishes a cryptographic code based on the computational complexity of mathematical problems. However, this type of cryptography, which is widely used in today’s telecommunications systems, is under threat as electronics and computing rapidly develop. The development of fifth-generation cellular networks (5G) is gaining momentum, and given its wide field of application, security requires special attention. This is especially true faced with the development of quantum computers. One solution to this security challenge is to use more advanced techniques to establish cryptographic keys that are not susceptible to attack. An essential part of quantum cryptography, Quantum Key Distribution (QKD) uses the principles of quantum physics to establish and distribute symmetric cryptographic keys between two geographically distant users. QKD establishes information-theoretically secure cryptographic keys that are resistant to eavesdropping when they are created. In this paper, we survey the security challenges and approaches in 5G networks concerning network protocols, interfaces and management organizations. We begin by examining the fundamentals of QKD and discuss the creation of QKD networks and their applications. We then outline QKD network architecture and its components and standards, following with a summary of QKD and post-quantum key distribution techniques and approaches for its integration into existing security frameworks such as VPNs (IPsec and MACsec). We also discuss the requirements, architecture and methods for implementing the FPGA-based encryptors needed to execute cryptographic algorithms with security keys. We discuss the performance and technologies of post-quantum cryptography, and finally, examine reported 5G demonstrations which have used quantum technologies, highlighting future research directions.
Keywords
DOI
https://doi.org/10.1109/COMST.2023.3309051
URL
Article is available via url: https://ieeexplore.ieee.org/document/10231341
Citation
M.Mehic et al. “Quantum Cryptography in 5G Networks: A Comprehensive Overview” IEEE Communications Surveys & Tutorials, 2023. doi: https://doi.org/10.1109/COMST.2023.3309051 SCIE Impact Factor: 35.6 (Q1/2022
Journal Title
IEEE Communications Surveys & Tutorials
Publisher
IEEE
Impact Factor
35.6 (2022)